Architecture deployed on Amazon Web Services
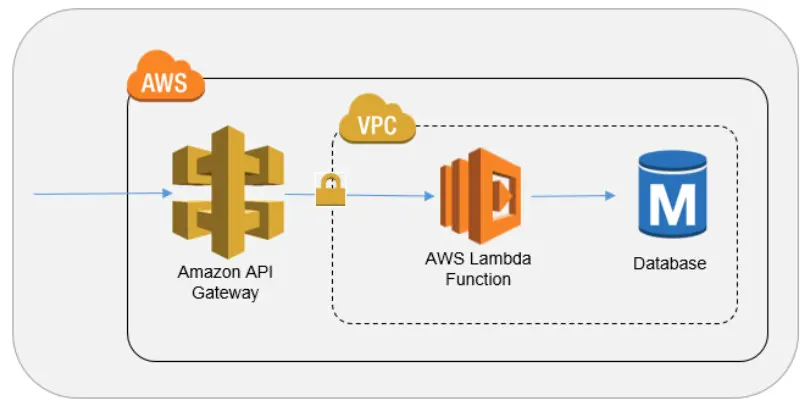
A serverless REST API on AWS uses Amazon API Gateway to receive HTTP requests and route them to AWS Lambda functions. These functions contain the business logic and respond to each request without needing to manage any servers.
The Lambda functions connect directly to a PostgreSQL database hosted on Amazon RDS. This setup allows the API to handle CRUD operations on persistent data. API Gateway takes care of routing, throttling, and authorization. Meanwhile, Lambda provides automatic scaling and pay-per-use pricing. Together, they offer a scalable and cost-efficient solution for modern cloud-native applications.
Deployment using AWS Chalice
To streamline the development of serverless APIs, developers can use AWS Chalice, a Python framework designed for AWS Lambda and API Gateway. It allows to define routes in a simple app.py file. As a result, endpoints deploy automatically to Lambda and become accessible through API Gateway, without requiring manual setup.
from chalice import Chalice
app = Chalice(app_name='api')
@app.route('/user')
def user():
return {'message': 'Hello from user!'}Chalice also manages packaging, IAM roles, and stage environments. It supports environment variables to securely connect to services like Amazon RDS. With just one chalice deploy command, you can launch a fully functional API available on the web!
Securing the serverless REST API
Security plays a critical role in serverless API design.
API Gateway must enforce authentication and authorization through AWS IAM or Amazon Cognito. This ensures that only trusted clients access the endpoints.
In addition, Lambda functions run inside a Virtual Private Cloud (VPC). This setup allows them to connect securely to the RDS PostgreSQL instance without exposing the database to the public internet.
Security groups and subnets add another layer of protection by restricting access to only essential resources, particularly the RDS PostgreSQL database.
To manage credentials safely, use environment variables. Also, assign IAM roles with the minimum permissions needed for each Lambda function. This follows the principle of least privilege.
When combined, these practices create a secure and robust foundation for cloud-native applications.
If you’re looking to implement a similar serverless architecture, I can help you design and deploy a tailored solution, learn more about my services.
